Settings
You can configure the following options:
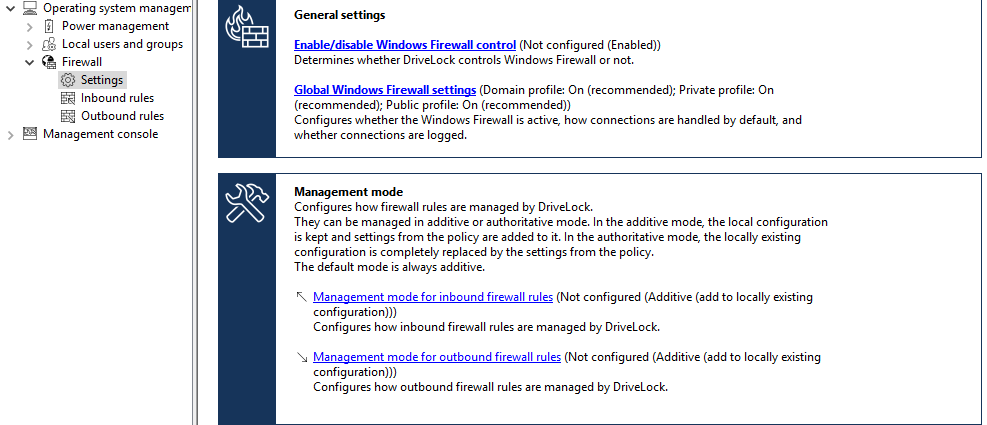
Enable/disable Windows Firewall control:
The setting has to be active to enable Windows Firewall control on DriveLock Agents. It is enabled by default. DriveLock will then be able to configure firewall settings, manage rules, and generate events related to the firewall.
Global Windows Firewall settings:
The global settings allow you to determine whether DriveLock manages the general Windows Firewall settings. You can also specify firewall settings for each network type and you can configure logging.
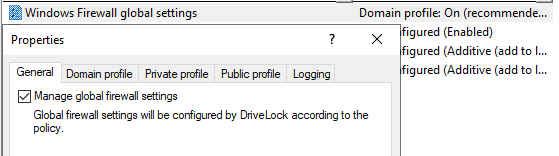
-
General tab: If you want DriveLock to configure the Windows Firewall according to the settings in this dialog, check Manage Global Firewall Settings. This setting does not affect the actual firewall rules. The rules are managed according to the policy, even if this setting is disabled.
-
Domain profile, Private profile and Public profile tabs: You can configure the firewall for each of the network types separately or configure it for the domain profile only and check the Use these settings for all profiles setting if you want all profiles to be configured the same.
The following options are available:
-
Firewall state: Select whether the firewall is on or off for the selected network type.
-
Inbound connections: Select whether to allow or block inbound connections for the selected network type. By default, inbound connections are blocked if none of the defined rules apply.
-
Outbound connections: Select whether to allow or block outbound connections for the selected network type. By default, outbound connections are allowed if none of the defined rules apply.
-
Display notifications to the user when a program is blocked from receiving inbound connections: Enable this setting if you want the user to receive a notification when the firewall blocks a connection for which no rule exists yet. By default, notifications are enabled.
-
Allow unicast responses to multicast or broadcast network traffic: Enable this setting if you want to allow unicast responses to multicast or broadcast requests within 3 seconds. We recommend that you disable this setting to avoid possible "denial of service" attacks. This setting does not affect DHCP. DHCP unicast responses are always allowed by the firewall. By default, this setting is enabled.
-
-
Logging tab: Here you can customize the logging settings. Select the connections you want to log.
The following options are available:
-
Log network connections: Check this option to log network connections. The default path for the log is
%windir%\system32\logfiles\firewall\pfirewall.log -
Log successful connections: Activate this setting to log successful connections.
-
Log dropped packets: Enable this setting to log dropped connections.
-
Ignore multicast packets while logging: Enable this setting to exclude multicast packets from logging.
-
Ignore connections using the following ports: Specify the ports to be excluded from logging.
-
Management mode for inbound or outbound connections:
The management mode determines how DriveLock manages firewall rules. Management can be either additive or authoritative.
-
In Additive mode, rules that exist locally are kept. The rules from the policy are only added. If the policy contains built-in firewall rules that also exist on the agent, these rules are modified according to the policy.
-
In Authoritative mode, existing rules on the agent are deleted and replaced with the rules in the policy. Existing built-in rules on the agent are only disabled by DriveLock and not deleted if they are not present in the policy.
Rules created via the group policy will remain in place. DriveLock neither modifies nor deletes them.
Rules that DriveLock creates for product functionality are not managed by DriveLock. They are always created and remain in the authoritative mode.
The default setting is additive.