Select trusted certificates
We recommend using this setting to increase the security requirements for communication between DriveLock Agent and DriveLock Enterprise Service. Unless you specify certificates, DriveLock cannot ensure that the agent is communicating with the right DES.
If you are using self-signed certificates,make sure to enter them here.
Certificates issued by a certificate authority (CA) can be verified by Windows.
There are two options when selecting trusted certificates:
-
If you are using the server certificate that you selected during the DES installation with the Create self-signed certificate option, select New in the context menu and then Server certificate (from DriveLock Enterprise Service) .
You can directly select the certificate used by the DES (or linked DES) (see figure).
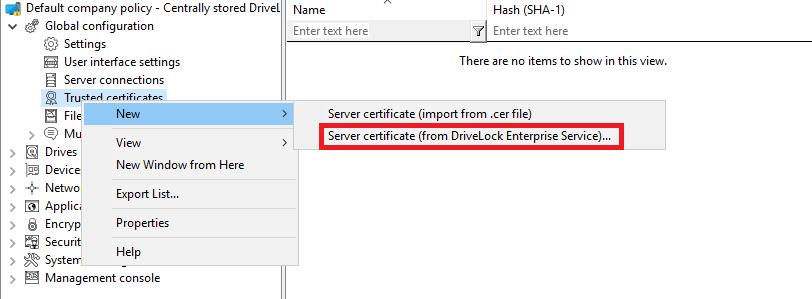
After that, place a check mark next to those DES (or linked DES) certificates with which the agent communicates (in the example below DLSERVER.DLSE.local...):
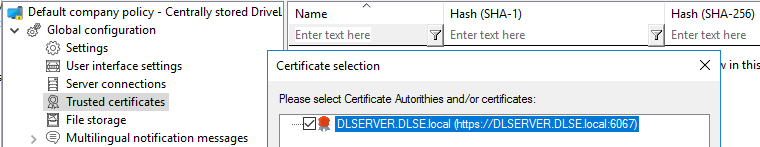
-
If you have specified your own server certificate for communication, you can select it here and use it in your policy:
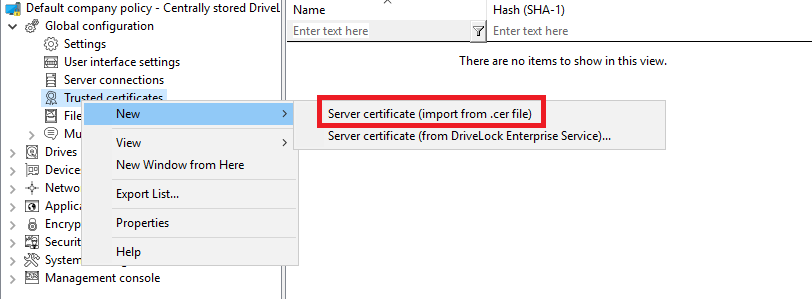
In the next step, select the appropriate certificate in the directory structure.
You can also import the root CA certificate with this option. This will make DriveLock agents trust all certificates with this root CA. If your DES certificates have the same root CA, you no longer need to list them individually.
The list of trusted certificates now displays the corresponding information about the certificate ( for example, name and hash values SHA-1 and SHA-256).
The DriveLock Agents to which you then assign your policy will trust the server certificate and communicate only with the appropriate trusted servers.