Terminal server rules
Depending on the connection type, the configuration takes place on the client or server side. It is important to set up an authorization concept by asking some questions: What do you want to block and which exceptions are required? How far do you go into detail? Do you need to unlock based on users/groups, on connected drive letters, on hardware data, or a combination of these?
Another distinction applies to the whitelist rules. At a minimum, permissions can be assigned based on the connected drive letter on the terminal server. Assigning permissions based on individual drives using the hardware data (e.g. USB stick Kingston DataTraveler) only works under certain conditions.
We recommended splitting the configuration of terminal servers and clients, for example, by employing a separate configuration.
Global configuration
The easiest case is to assign permissions to all connected drives of a client. It does not matter what kind of drive is connected, for example a hard disk or a USB stick. Permissions are implemented for all these connected drives based on users or groups. A distinction is made here according to the connection protocol: (Advanced Configuration ->) Drives -> Removable drive locking
- Windows Terminal Services (RDP) client drive mappings: All connections via RDP, Windows default.
- Citrix XenApp (ICA) client drive mappings: All connections via ICA, Citrix standard. Requires Citrix Presentation Server 4.5 (64-bit) or XEN 5 or above.
Based on the connected drive letters
To lock drives, you need to configure the Terminal Server environment to use predefined drive letters for certain drive types (e.g. USB removable drives). This can be set on thin client side. Then you can create a Terminal Services rule to set permissions or time restrictions on this drive letter.
Example: A user connects to a terminal server. The client is a thin client. All thin clients are configured by the administrator to always mount USB drives as drive U: within the terminal server session. The administrator creates a Terminal Services rule in DriveLock for the U: drive and assigns permissions to a group on it. In this way, access to USB drives can be controlled via the group.
To create an exception based on the connected drive letters, navigate to Drives: Drive whitelist rules, then right-click on it to New -> Terminal services rule....
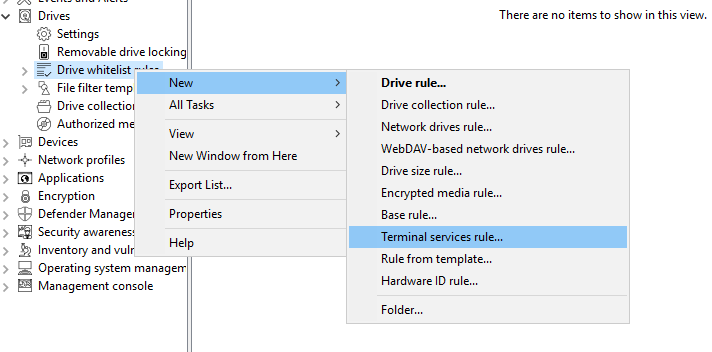
Next, select a letter from the drop-down menu and activate the appropriate protocol that is used in your environment. Permissions are assigned on the Permissions tab:
Based on the hardware data
If you want to create a whitelist rule based on the hardware data, the connection type allows it, you can create a rule as usual: Drives -> Drive whitelist rules -> Drive rule.... and then connect to the client or terminal server, depending on the connection type, and select the drive to be shared. Then, assign the permissions on the Permissions tab.
File filter
The file filter can be used to restrict and log accesses based on file types (PDF, DOCX, etc.). However, the file filter must have been created beforehand.
The file filter can be used and assigned in all rules. In general, the client-side file filter is more powerful than server-side. Restrictions due to the connection types can be found in the overview table in chapter Connection types.
A file filter can be applied to all types of rules.
In the following example, we use a file filter template (which locks executable files), and apply it server-side to connections made using the ICA protocol: Drives -> Lock Settings -> Citrix XenApp (ICA) Client Drive Mappings -> Filter /Shadow tab.
After that, there are the following options:
- Filter files [...]: file types are allowed/blocked based on the selected file filter template.
- Audit and shadow files [...]: Operations (read, write) are logged and can be evaluated later with the DOC.
- Allow access as configured only to selected subfolders: Here you can configure folders by clicking this button.