The Execution options tab
You can select options for starting and delaying encryption, and for forced encryption on this tab.
You can configure whether BitLocker encryption on the DriveLock Agent should start depending on certain events, or whether the user can delay the encryption. The objective is to disturb the user as little as possible and to keep the computer performance constant without compromising the protection provided by the encryption.
You can only select the Start enforced encryption after x hours option if you have selected the BitLocker PBA in the Pre-boot authentication settings and specified a password there. If the user has not assigned their own password by the time the specified time expires, encryption will be performed using the specified password. The counting starts the moment when the password dialog is displayed for the first time.
With the Encrypt hard disk independently of user interaction (only possible if TPM is enabled), you can ensure that an agent's hard disk is encrypted even if the user has not yet logged on to the DriveLock PBA or has not yet entered a password for the BitLocker PBA. This option is only effective if TPM is active on this system.
With the Start encryption only in the following events: option you can specify conditions when encryption may start. For example, if you want to specify that encryption should start only on a client computer if no users are logged in, check the option as illustrated in the figure below:
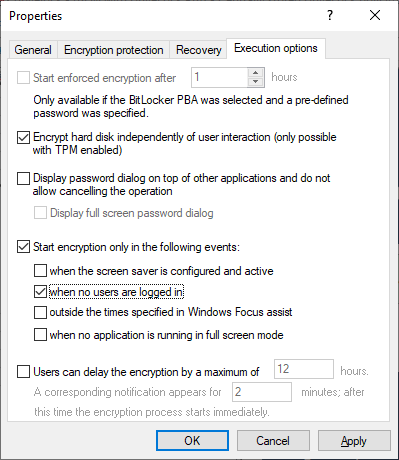
When selecting the option when no application is running in full screen mode, make sure that the application is actually running in full screen mode and not just maximized. This option is particularly important when running CAD/CAM applications, for example.
In the lower section, you specify the maximum number of hours users are allowed to delay encryption. A value of up to 9000 hrs. is possible here. You also specify how long the delay notification is displayed to the user. Once this time has expired and the user has taken no action on their client computer, the encryption will start automatically. The same applies if no user is logged in.
As soon as the user receives the delay notification, encryption will start and the protectors will be created automatically. Immediately after that, encryption is paused and then resumes once the user clicks Encrypt in the notification or the delay time expires (without user interaction). Then encryption continues. The system is already secure at that point and the user must already provide a password (or PIN in the case of TPM) when rebooting.