BitLocker Management in the DCC
In the DriveLock Control Center’s Helpdesk view, click Encrypted Disks to view all computers with encrypted and/or decrypted hard drives.
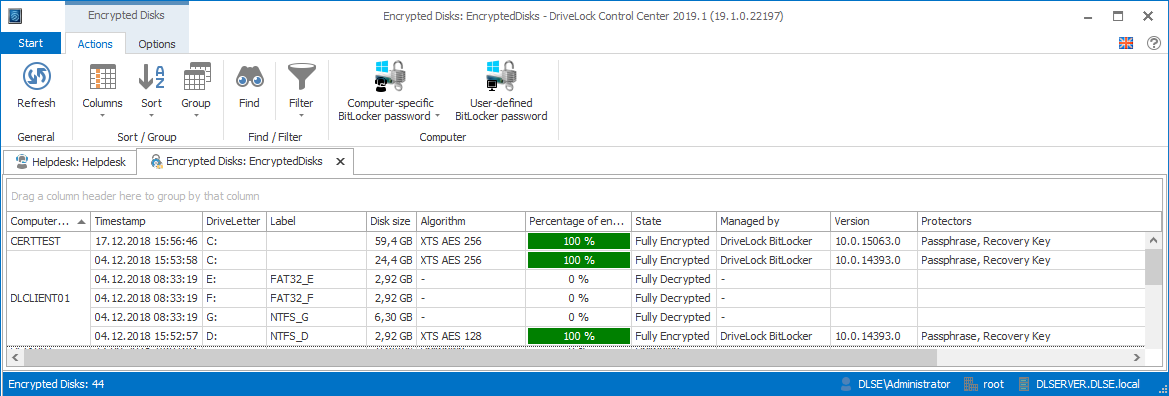
The following information, among others, is displayed here:
- Algorithm: this column shows the algorithm used to encrypt the respective drive and which you set in the Harddisk encryption settings dialog.
- Percentage of encryption: if the drive is completely encrypted, the percentage shows 100%. During the encryption or decryption process, you can see how much of the data is encrypted in percent.
-
State of encryption with the following values:
- Fully Decrypted: the drive is decrypted. The data is not protected.
- Fully Encrypted: the drive is encrypted.
- Encryption In Progress: the drive is currently being encrypted. See how much of the drive is already encrypted in the Percentage of encryption column.
- Decryption In Progress: the drive is currently being decrypted. The percentage refers to the portion that is still encrypted.
-
Locked: This state shows that a drive has already been encrypted with native BitLocker before being managed with DriveLock BitLocker Management (i.e. before the installation of the DriveLock Agent and before assigning a BitLocker policy).
Please find more information in the topic Integrating existing BitLocker environments.
-
Managed by shows whether DriveLock is already managing the encryption or still native BitLocker.
- DriveLock BitLocker: DriveLock BitLocker Management is already managing the drive.
- BitLocker: Native BitLocker is still locking the drive (see above). The drive has to be unlocked so that it can be accessed by the DriveLock Agent, re-encrypted and managed by DriveLock BitLocker Management.
-
Protectors:
- Passphrase: If the Trusted Platform Module (TPM) is missing or not enabled on the computer, a passphrase can be used for authentication. Users must enter this passphrase each time they start their computer in the Windows pre-boot environment.
-
Recovery Key (also Numerical Password): The recovery key is always used as a protector for encryption.
Microsoft uses two protectors by default for the original encryption of a system or data partition with BitLocker. These are either TPM, TPM and PIN or Passphrase and Numerical Password.
-
TPM: This protector only works on drives with a built-in TPM (’TPM only’). Entering a PIN (BitLocker password) is not required.
- TPM and PIN: A built-in TPM is also required in this case. Here the TPM and a PIN (BitLocker password) are used for authentication. Users must enter this password each time they start their computer in the Windows pre-boot environment.
-
External Key: DriveLock uses this protector if the auto-unlock option is specified for the drive (Automatically unlock all data partitions in the Authentication type dialog).
DriveLock also provides the recovery key for data partitions. Even without the auto-unlock option, this external key allows you to access a data partition that is not protected with a password. This ensures that data partitions can also be unlocked using the recovery key, even if TPM is used as the protector.