Hard disk encryption settings
The General tab
On this tab you set the values for encryption and decryption with BitLocker.

The following options are available:
-
Encrypt local hard disks on Agent computers:
-
Select this option to start the encryption of the hard disks with BitLocker. Before you do so, make sure that all other encryption settings (see below) are specified.
As soon as you check this option and the policy has been assigned and updated on the client, the encryption process starts.
-
To allow decryption (see detailed description in chapter decryption), uncheck the option and, if necessary, specify a delay in days.
Once you uncheck the option and do not specify a delay (and the policy is assigned and synchronized by the client), the decryption process will start.
-
-
Encryption algorithm priority:
-
The list of the different encryption methods is processed from top to bottom. Once BitLocker Management finds a suitable algorithm that can be applied to the client, it will use it for encryption.
We recommend placing the strongest algorithm at top level.
- You can also sort the algorithms manually according to your requirements.
-
Hardware encryption algorithm:
This is a special algorithm some producers build in to their hard disks. If you want to use this algorithm, please move it to the top of the list.
-
Example:
You may want to move the AES with Elephant diffuser (128 or 256 bit key length) entry up if you have many computers with Windows 7 systems to encrypt, so that this algorithm is preferred.
-
-
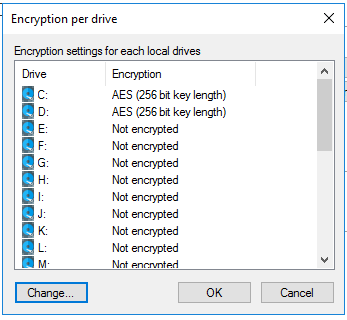
Configure encryption settings per drive:
-
Select the required encryption algorithm for the system drive and the data drives by clicking the Settings button or choose 'Not encrypted' if no encryption is required.
Please ensure that the drive letter and system partition assignment is the same for all computers this BitLocker policy is assigned to.
-
-
Initial encryption
-
Encrypt only used disk space (fast initial encryption):
- Select this option if you want to encrypt only the used disk space.
-
Background:
With Windows 8, BitLocker introduced a feature that the hard disk does not have to be fully encrypted, but only the part where data is stored. Encryption is much faster for this reason.
-
Issue:
Data that has been deleted from the hard disk and that is no longer visible in the Explorer may actually still exist and the original data can be accessed with special tools.
We recommend that you only enable this option if you want to encrypt new hard disks, for example. Make sure that there is no old sensitive data on the hard disk. Likewise, this option is recommended for all SSDs.
-
Display warning when disks are not fully encrypted
Each time the system is rebooted or the DriveLock Agent is restarted, the system checks whether all hard disks are already fully encrypted according to the settings. If this is not the case, the user is notified accordingly.
-
-
Settings for native BitLocker
-
Manage native BitLocker environment
Select this option if you want to manage existing (native) BitLocker environments with DriveLock BitLocker Management. Please refer to chapter Integrating existing BitLocker environments for more information.
Once you select this option and assign the policy accordingly, a wizard opens on the client computers with native BitLocker-encrypted (and thus locked) data drives; this wizard prompts the user to take over the drives. This is where you must provide the passwords for the locked partitions before they can be taken over.
-
Hide native BitLocker context menu entries
This option is enabled by default. It hides all BitLocker options in the Windows Start menu or in the Explorer so that the native BitLocker dialogs are not displayed. This limits the chance of accidentally encrypting a hard disk or a drive with BitLocker but without DriveLock.
-
-
Installation protection
-
Encrypt only if pre-boot logon succeeded at least once
This is a preventive measure that keeps encryption separate from the initial logon to the PBA. Encryption is delayed until the first logon is successful.
-
-
Response to configuration changes
-
Delay decryption by [x] days:
This setting delays the decryption for the specified number of days. This may be useful so that the client computers and their users can be properly prepared for decryption.
The default value is 3 days. This value provides additional protection against misconfiguration. If you want to perform decryption immediately, change the setting to 0 days.
-
Do not decrypt:
This option is enabled by default. Its purpose is to prevent unintentional decryption of BitLocker encryption when the configuration is changed, for example, after DriveLock Agent updates, if group memberships are changed, or if the policy is no longer used by the DriveLock Agent.
Note that decryption is triggered only by disabling the Encrypt local disks on agent computers option described above. Decryption starts once the DriveLock Agent receives the configured policy with the mandatory decryption setting.
-
The Recovery tab
On this tab you specify where the encrypted recovery data should be stored. These are the settings you need when you start the recovery process.
The following option is currently available:
-
DriveLock Enterprise Service:
Select this option if you want to send the encrypted recovery data to the DriveLock Enterprise Service (DES).
-
File server (UNC path)
If you select this option, your encrypted recovery data is stored on a server, for example. When you select this option, you can specify a user name and password under the Log in to file server option.
-
Local folder on Agent computers (not recommended)
We recommend this option only if you store the key files on a secure storage medium (e.g. USB device) or move them to a secure location later.