Application hash database
To facilitate application control configuration, DriveLock provides the option to create application hash databases and use them in whitelist or blacklist mode. Hash databases can be created by automatically searching for applications in a directory or directories (and their child directories), calculating their hash values and saving them to a file. A hash database of all installed programs can also be created from the hard disk of a reference system.
Follow these steps to create an application hash database:
- In the Applications node, select Application rules. Next, select New from the context menu and open the Application hash database dialog.
- Initially no database is selected on the General tab. You can either create a new database file or select an existing one.
DriveLock provides a utility program DriveLock Application Hash Database Tool that can also be used to generate a hash database. The utility is located in the installation directory of DriveLock (C:\Program Files\CenterTools\DriveLock MMC\Tools\DLExeHasher.exe).
- The value that is already preset in the hash procedure is listed in the Hash algorithm used in database section.
-
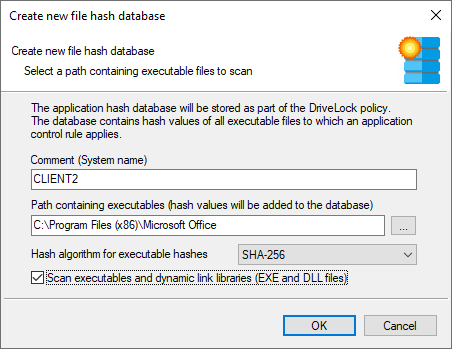
To create a new database, click Database file and then click Create new.
-
In the Comment (System name) box, type the name of the computer to be scanned. With this information, it is easier to assign multiple database files during a migration at a later date. Type or click ... to select the directory to be scanned for applications.
You can scan a directory on a remote computer by specifying the UNC path for this directory.
The Hash algorithm for executable hashes defines the algorithm used for this database. Initially the general hash algorithm is set here. Select Scan executables and dynamic link libraries to scan DLL files in addition to EXE files.
-
Click OK. DriveLock starts a recursive scan of the specified directory and all child directories below it.
Please note that scanning larger directories or UNC paths may take some time. Please do not interrupt the process.
No duplicate entries are generated during the search. If it finds the same file in a different directory, DriveLock does not add the hash value to the hash database again. This has no effect on how the rule is applied because applications are evaluated based on their hashes and not a specific location. Also, this behavior allows for differential scanning, which only adds applications that are not already in the database.
-
When DriveLock has finished detecting all program files and has calculated all hashes, it adds all applications it detected to the template and displays the previous dialog box.
-
Add a description (Rule name) and enter additional information in the Comment text box if necessary.
-
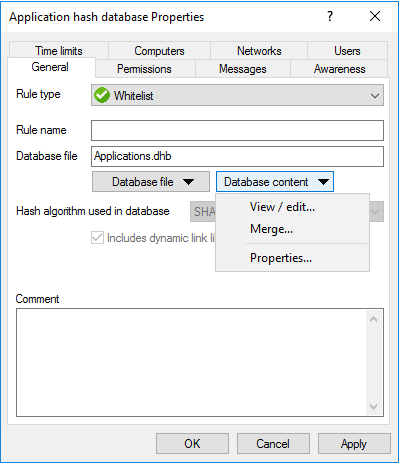
Click Database content to view, edit or merge the programs that are included in the database.
-
Click Database content and then click View / edit to view the database content.
-
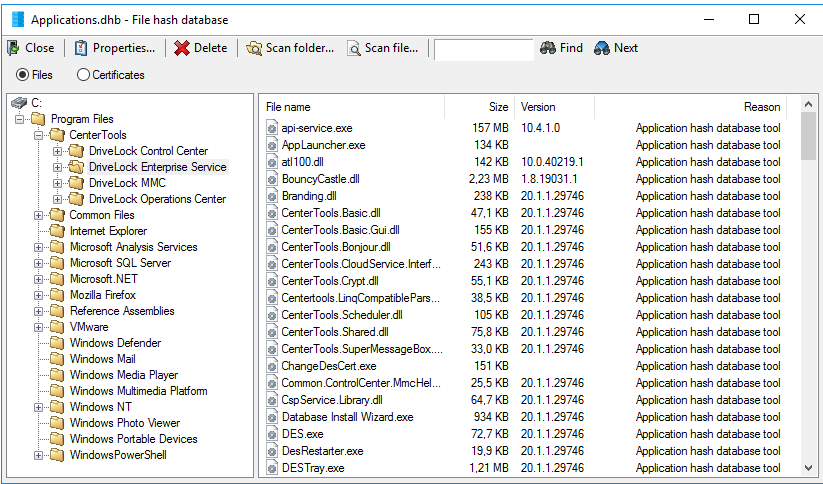
The left pane displays the folders that were scanned. Select a folder to display all programs that were found in this folder in the right pane.
-
To add additional hashes, click Scan folder or Scan file. Click Delete to remove the selected application hash or folder. To view additional information about the hash database, click Properties.
-
To close the hash database viewer, click Close.
You can also use the standalone Application Hash Database Tool, DLExeHasher.exe, to view, edit and merge hash databases.
-
Click Database content and then click Merge to add the content of another database.
-
Type or select the path of the database file containing the entries to be added. Alternatively you can use the file selection dialog.
-
Click OK so that DriveLock merges the database content.
-
Then it displays the template properties again.
-
Click OK to exit the dialog and save the changes.
Even if you are using a whitelist rule based on a hash database of all installed applications to control a computer, it is recommended that you also use some special application rules for programs that are part of the operating system. For technical reasons, they are loaded faster than the information from the hash database and are therefore made available to the DriveLock Agent much sooner when Application Control is started.